Nowadays, attacks from Botnets such as DDoS or phishing are becoming more and more common, that is why it is advisable to always have global block rules in corporate firewalls in the top of your firewall policy.
In the case of Fortigate NGFW and with just the basic hardware license “forticare”, you can make use of Fortiguard's public IP databases called “Internet service”.
This IP database is automatically updated by Fortiguard and includes the new IPs to all internet service objects.
As a standard practice I recommend creating two firewall rules that block the following internet objects:
Outgoing traffic to the next internet objects to be blocked:
- Botnet-C&C.Server
- Phishing-Phishing.Server
- Proxy-Proxy.Server
- Spam-Spamming.Server
- Tor-Exit.Node
Incoming traffic to the next internet objects to be blocked:
- Botnet-C&C.Server
- Phishing-Phishing.Server
- Proxy-Proxy.Server
- Spam-Spamming.Server
- Tor-Relay.Node
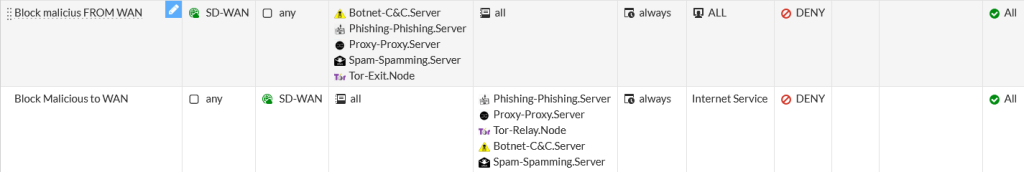
Screnshot firewall rules :
CLI Code:
config firewall policy
edit 0
set name "Block malicius FROM WAN"
set srcintf "SD-WAN"
set dstintf "any"
set dstaddr "all"
set internet-service-src enable
set internet-service-src-name "Botnet-C&C.Server" "Phishing-Phishing.Server" "Proxy-Proxy.Server" "Spam-Spamming.Server" "Tor-Exit.Node"
set schedule "always"
set service "ALL"
set logtraffic all
next
end
config firewall policy
edit 0
set name "Block Malicious to WAN"
set srcintf "any"
set dstintf "SD-WAN"
set srcaddr "all"
set internet-service enable
set internet-service-name "Phishing-Phishing.Server" "Proxy-Proxy.Server" "Tor-Relay.Node" "Botnet-C&C.Server" "Spam-Spamming.Server"
set schedule "always"
set logtraffic all
next
end